Shadow Risk Detection & Elimination
A paradigm shift in how vulnerability assessment is done, powered by CyCognito
Intelligent-Data is an authorized reseller of this Nation State Reconnaissance platform
See Exactly What Attackers See.
Identify and eliminate your shadow risk by mapping your organization’s attack surface and attack vectors.
Do you know your shadow risk?
Are you as protected as you think from 2nd & 3rd party ‘partners’ ?
“Digital risk and digital trust are dynamic and vary over time based on context. Thus, risk is calculated for vulnerability management on a continuous basis to calculate the risk exposure of an organization. For example, a vulnerability may not be a significant risk today, but it can materialize into a severe risk to an organization overnight. If a continuous risk assessment is not deployed, the organization will miss addressing the risk, resulting in fatal consequences.”
Intelligent -Data is an authorized reseller for the use of a Nation State Reconnaissance platform that reveals & eliminates attackers paths of least resistance.
NO – on site agents used
NO- permissions requested
NO- IP addresses information requested.
The vulnerability assessment platform that goes beyond a pen test, and far beyond the old vulnerability on/in network scanners.
Increased IT Complexity Impacts Security.
The CyCognito platform helps you identify all of the attacker-exposed assets in your IT ecosystem for a complete view of your attack surface. With its comprehensive global botnet, the CyCognito platform uniquely reveals unknown and unmanaged assets associated with your organization – including those of partners and subsidiaries – that are critical to your cybersecurity risk management.
ATTACK SURFACE VISIBILITY
Map Attack Surfaces.
CyCognito shows you how attackers view your organization and where they are most likely to break in. Our SaaS platform helps you quickly see and rank your most critical risks and gives you prescriptive remediation guidance so you know precisely where and how to focus your security team to eliminate them.
Continuously identify the critical weaknesses in your IT ecosystem that are most attractive to attackers.
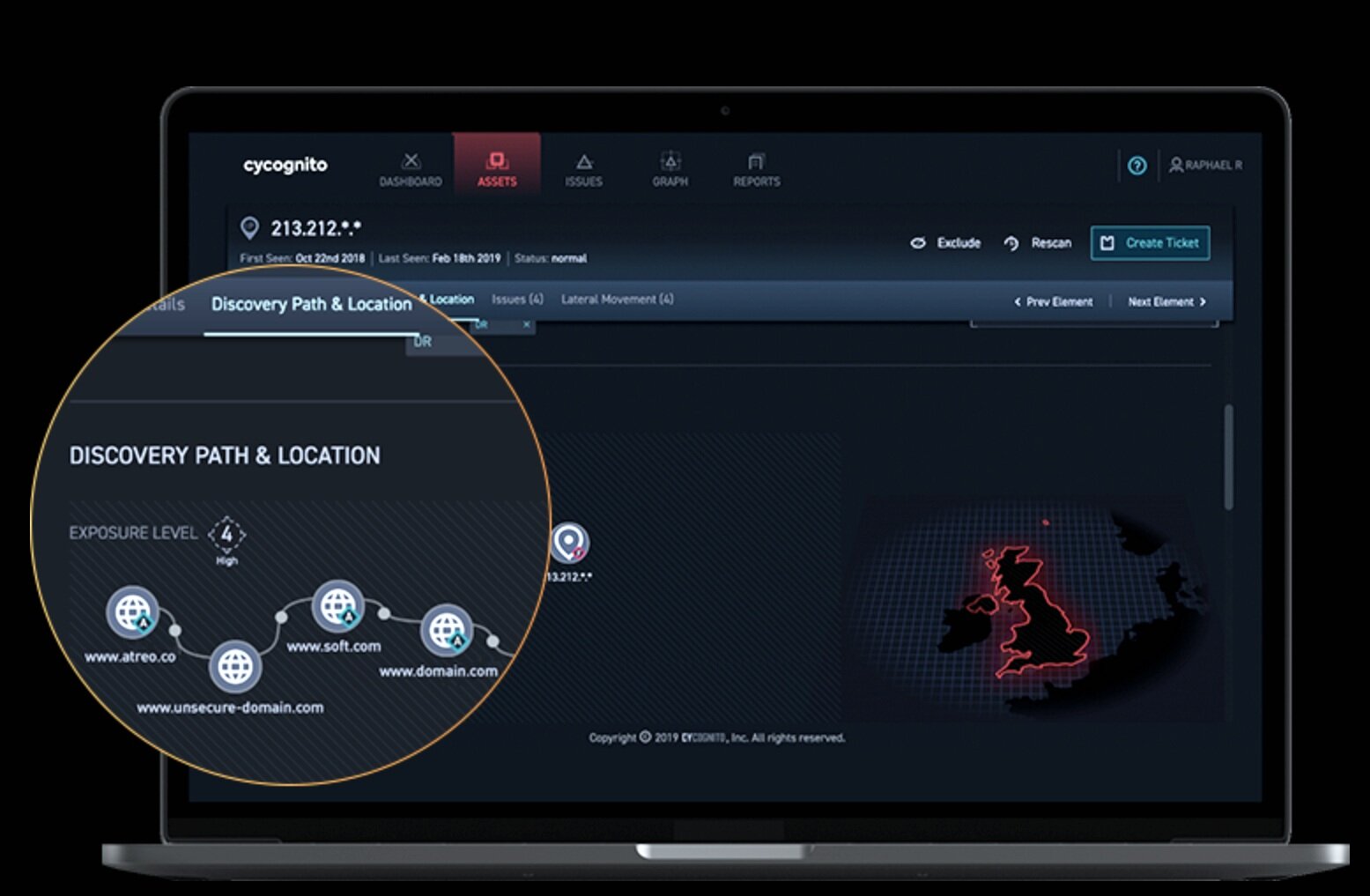
The botnet and discovery engine use graph data modeling to map and classify the assets across your attack surface.
RISK-BASED VULNERABILITY MANAGEMENT
Measure and manage your security performance with the CyCognito platform to fully understand and improve your cybersecurity posture. The automated self-assessment is built upon a detailed analysis of the business context and risk of each individual IT asset in your attack surface.
Discover and prioritize security risks introduced by your subsidiaries, partners, M&A candidates and cloud services. Identify the breadth of a target organization’s attack surface and rates the effectiveness of its security controls, without requiring any deployment or configuration.
IT ECOSYSTEM RISK MONITORING
Get Actionable Remediation Guidance.
The platform delivers prescriptive remediation guidance for each of the identified risks so your security teams know precisely where and how to eliminate them.
The CyCognito platform helps you identify and eliminate your shadow risk by mapping your organization’s attack surface and attack vectors.
Monitor the entire attack surface for new assets, classifications and ownership attribution to understand your vulnerabilities.
Effective Cybersecurity and Risk Management Starts Here.
The CyCognito platform helps you maintain a continuously updated and prioritized view of your attacker-exposed IT ecosystem. You and your security team can use the CyCognito platform to pinpoint critical risks just as attackers do.
Organizations that still have to perform legacy external testing to meet customer agreements or compliance regulations use the CyCognito platform to augment and optimize those processes by focusing the legacy tests on the areas of greatest risk that the CyCognito platform has identified.
Wouldn’t it be great if the platform could answer these most desired questions/features?
To catch a hacker’s path- the CyCognito platform, must think like a hacker.
Without input or configuration, the CyCognito platform automates attacker reconnaissance at-scale, applying advanced analytics to identify, prioritize and eliminate unknowns.
How it’s Different
CyCognito represents a true paradigm shift in how vulnerability assessment is done! The CyCognito platform utilizes the largest ‘good Botnet’ that goes on the offense and far BEYOND your own networks’ external risks. This platform preforms attack simulations continuously, with no false alarms and doing no harm.
Today’s new expanded ecosystems is - in the Cloud, 2nd & 3rd party partners, IaaS, IoT, and SaaS platforms and applications
That is Your Shadow Risk
Intelligent-Data news.
Sign up with your email address to receive news and updates.